Subscribe to our blog
Thanks for subscribing to the blog.
February 10, 2021
Topics: Cloud Insights Advanced3 minute read
Why it’s so difficult to stop ransomware in financial services
The thing that makes ransomware impossible to prevent, and so difficult to detect until it’s too late, is that it masquerades as a trusted user of your data. A trusted user is a person or application that is able to access the data and is required to do so in order to conduct business as usual.
This requirement means that many ransomware detection tools search for data access patterns that don’t look like your average user activity, such as sudden spikes in file activity.
But what happens when your critical business processes create activity that looks like ransomware? Many companies in the financial services industry are increasingly frustrated with this issue.
And one financial services organization found out the hard way—twice.
This organization found that their risk-modelling application accessed files in bursts in a way that triggered malware protection, putting a seriously disruptive halt to business-critical operations. This disruption became so regular that they had no choice but to disable protection—and you can probably guess what happened next.
With file protection removed it was only a matter of time before malware found its way into the environment through a user who had a momentary lapse in security awareness.
The organization needed a better solution that would allow users and applications to access the data that they needed to do their jobs while simultaneously detecting ransomware without false positives.
Enter NetApp® Cloud Insights and the Cloud Secure ransomware detection feature.
With Cloud Secure, you don’t need to define specific rules or thresholds to detect what’s malicious and what’s business as usual. Instead, Cloud Secure relies on learning what normal looks like, such as burst access by a risk-modelling application, so it can minimize false positives but still trigger protection when it detects something out of the ordinary.
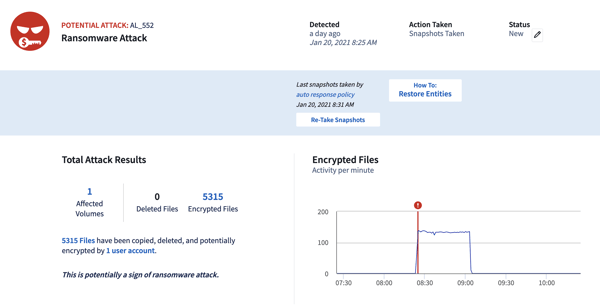
Protection doesn’t stop there, though. Close integration with NetApp storage means that instead of locking out users or applications when a potential threat is detected, a NetApp Snapshot™ copy can be triggered. This copy protects data from that point onward without disrupting applications. Administrators monitoring the systems can then investigate the activity and take further action if necessary, while knowing that data is protected if it comes to the worst.
Try Cloud Insights for free in your own environment for 30 days. You’ll gain access to our ransomware detection features, and also to monitoring, alerting, and metrics visualisations across all your infrastructure and applications, whether they’re on your premises or in the cloud, NetApp or third party.