Subscribe to our blog
Thanks for subscribing to the blog.
March 16, 2020
Topics: Cloud Data Sense Advanced9 minute read
At the beginning of 2020, the National Institute of Standards and Technology (NIST) published a set of guidelines that will help enterprises adapt to today's landscape of increasingly demanding data privacy requirements.
The NIST Privacy Framework: A Tool for Improving Privacy through Enterprise Risk Management is a voluntary set of procedures, which can aid compliance with different data protection regulations across the world.
The NIST framework is set to have major implications for organizations based in the US, where data privacy legislation is highly fragmented. It could even pave the way for harmonization of data privacy laws across the country.
This data privacy framework provides a structured approach to data privacy management and is designed to support privacy-by-design concepts. But what is NIST and what exactly does the NIST data privacy framework document set out to achieve?
This post gives you the background to the new framework and explains all the key concepts.
What Is NIST?
 The National Institute of Standards and Technology (NIST) is a non-regulatory federal agency that promotes innovation and industrial competitiveness by advancing technology and developing metrics and standards. It is part of the US Department of Commerce and was previously known as the National Bureau of Standards (NBS). It provides services to many industries, including healthcare, construction, manufacturing, and communications.
The National Institute of Standards and Technology (NIST) is a non-regulatory federal agency that promotes innovation and industrial competitiveness by advancing technology and developing metrics and standards. It is part of the US Department of Commerce and was previously known as the National Bureau of Standards (NBS). It provides services to many industries, including healthcare, construction, manufacturing, and communications.
Aims of the Framework
The new NIST Privacy data privacy guidelines are an organized framework through which enterprises will be able to map privacy requirements with specific workflows and controls. It is a high-level, technology-neutral guide that will aid senior management in making company decisions about data privacy without the need for strong technical insight.
The framework will give organizations a sense of structure to their data privacy strategies and help them comply with not only new laws coming into force, but also existing regulatory frameworks such as the Health Insurance Portability and Accountability Act (HIPAA) and the EU General Data Protection Regulation (GDPR).
It will help organizations identify gaps in data protection coverage by bringing to attention data privacy issues they may have overlooked. And it also provides a common language for privacy management across an organization and different external parties that handle its data.
The framework is flexible, scalable and extensible, making it suitable for any size of business, and is ideal to those who are relatively new to compliance but don't where to start.
However, it will be equally useful to enterprises that already have well-established data privacy procedures—by using it as a tool to formalize existing practices, develop improved, adaptable and future-proof data protection strategies and support accountability.
Alignment with the NIST Cybersecurity Framework
The privacy document is designed for use in tandem with NIST's Cybersecurity Framework. They use a common structure and overlapping catalogs of controls that work in harmony with one another, thereby streamlining the work you need to implement both sets of guidelines.
This alignment makes sense, as security and privacy are complementary—although not one and the same.
For example, privacy deals with many concerns that are outside the scope of cybersecurity, such as:
- collecting only the information you actually need
- being transparent about your use of personal data
- maintaining the privacy rights of individuals
The framework also sets out an approach for distinguishing between a privacy event and cybersecurity incident, defining a privacy event as an issue that could potentially have an adverse impact as a result of the way you process data. For instance, this might be:
- misuse of information
- unwelcome and intrusive surveillance
- denial of a data subject's privacy rights
However, cybersecurity and privacy risks overlap where potential cybersecurity incidents could lead to negative effects on individuals.
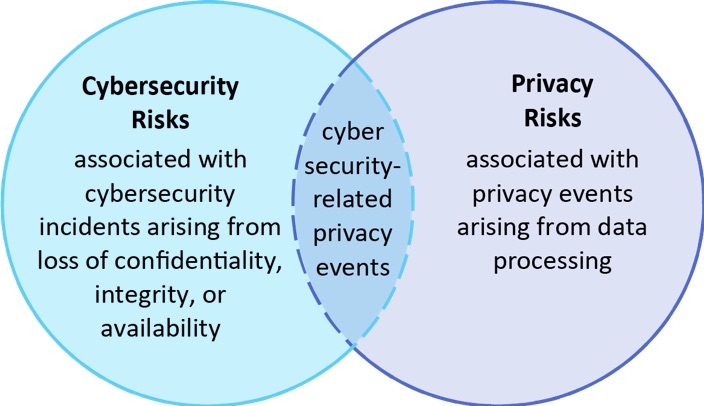 Relationship between Cybersecurity and Privacy Risks (Source: NIST Privacy Framework document)
Relationship between Cybersecurity and Privacy Risks (Source: NIST Privacy Framework document)
Key Framework Concepts
As well as following the same structure, NISTs privacy and cybersecurity frameworks also share common basic concepts and terminology. The following are the most important to understanding and implementing the privacy framework.
Core
The core is one of three foundational components to the framework structure. It comprises a set of five broadly based privacy protection activities or desired outcomes, known as functions. These functions are:
- Identify-P: Identify privacy risks by means of an inventory, data mapping and risk assessments including due consideration to the roles and responsibilities of third-party processors.
- Govern-P: Govern privacy risks through policies, processes and procedures, a risk management strategy, monitoring and reviews, and awareness and training.
- Control-P: Control privacy risks by means of data processing policies, processes and procedures, data processing management and processing without association to individuals or devices.
- Communicate-P: Communicate privacy risks by raising data processing awareness and developing communication policies, processes and procedures.
- Protect-P: Protect against privacy risks using data protection policies, processes and procedures, identity management, authentication and access control, data security, system maintenance, and protective technology.
The framework breaks down each function into categories and subcategories in order to describe more specific requirements or outcomes.
The following excerpt from the NIST framework is part of a table showing a category and several subcategories for function Identify-P:
|
Function |
Category |
Subcategory |
|
IDENTIFY-P (ID- P): Develop the organizational understanding to manage privacy risk for individuals arising from data processing. |
Inventory and Mapping (ID.IM-P): Data processing by systems, products, or services is understood and informs the management of privacy risk. |
ID.IM-P1: Systems/products/services that process data are inventoried. |
|
ID.IM-P2: Owners or operators (e.g., the organization or third parties such as service providers, partners, customers, and developers) and their roles with respect to the systems/products/services and components (e.g., internal or external) that process data are inventoried. |
||
|
ID.IM-P3: Categories of individuals (e.g., customers, employees or prospective employees, consumers) whose data are being processed are inventoried. |
||
|
ID.IM-P4: Data actions of the systems/products/services are inventoried. |
||
|
ID.IM-P5: The purposes for the data actions are inventoried. |
||
|
ID.IM-P6: Data elements within the data actions are inventoried. |
||
|
ID.IM-P7: The data processing environment is identified (e.g. geographic location, internal, cloud, third parties). |
||
|
ID.IM-P8: Data processing is mapped, illustrating the data actions and associated data elements for systems/products/services, including components; roles of the component owners/operators; and interactions of individuals or third parties with the systems/products/services. |
Profiles
A profile is a set of specific functions, categories and subcategories that your organization selects from the framework based on its most important priorities for managing privacy risk.
You can create a profile to describe the current state of your privacy undertakings and also the target state representing where your organization wants to be.
In essence, you select each combination of function, category, and subcategory based on the individual needs and objectives of your organization—taking into account factors that dictate your risk management strategy, such as:
- regulatory requirements
- your products and services
- shared privacy responsibilities with external parties
You can use profiles to identify gaps in data privacy and protection, draw up an action plan to address them and measure progress.
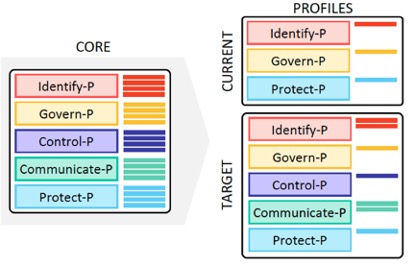 The Relationship between the Framework Core and Profiles (Source: NIST Privacy Framework document.)
The Relationship between the Framework Core and Profiles (Source: NIST Privacy Framework document.)
Implementation Tiers
Implementation tiers, which move progressively upwards from Tier 1 to Tier 4, indicate the strength of privacy measures your company either currently applies or is aiming to achieve.
They are largely intended as general benchmarks for gauging improvement in your company's capability to manage privacy risk.
Risk Management Approaches
In addition, the document briefly discusses how to address privacy risks through the following four response approaches:
- Mitigation: Integrating data privacy measures into your IT systems, organizational processes, and products and services.
- Transfer: Delegating the responsibility to third parties, such as a cloud service provider, or using a consent mechanism to share responsibility with data subjects.
- Avoidance: Ceasing data collection where the risks outweigh the benefits.
- Acceptance: Concluding that remedial action is unnecessary on account that potential damage is either minimal or highly improbable.
A Step in the Right Direction
Owing to the patchwork nature of data protection laws in the US, the new NIST Privacy Framework is a welcome and long-overdue step towards a more consistent approach to data privacy. It will also help bring privacy into parity with the broader enterprise risk portfolio.
Although not mandatory, following the NIST framework offers the potential to realize significant benefits, helping you to build trust, demonstrate accountability and become better placed to comply with new regulations in the future.
But, above all, the NIST data privacy framework outlined above is designed for privacy professionals with little or no technical knowledge. So you can get to work on the framework practically straight away.
How can you enact policies in line with the NIST framework? For Amazon S3, Azure NetApp Files, and Cloud Volumes ONTAP users, the new Cloud Compliance add-on feature has capabilities that can meet the NIST core functions outlined above:
- Data Mapping for Identify-P: Cloud Compliance maps all the data that is stored in your cloud repositories, identifying privacy risks.
- Easy reporting for Govern-P and Communicate-P: Reports on data mapping can be produced easily, allowing demonstration of compliance and privacy including Data Subject Access reports and data breach impact analysis reports.
- Control-P: Control privacy risks by means of data processing policies, processes and procedures, data processing management and processing without association to individuals or devices.
- Identify where sensitive data exists for Protect-P: Data mapping allows you to identify and isolate sensitive private data to make sure it is properly protected.
The NIST guidelines discussed in this article can be found here and also freely available for immediate download from the NIST website.
