Subscribe to our blog
Thanks for subscribing to the blog.
April 20, 2020
Topics: Cloud Volumes ONTAP Data ProtectionGoogle CloudAdvanced5 minute readSecurity
Google Persistent Disk is a fundamental part of the Google Cloud Compute Engine service. It provides persistent storage management capabilities to Google Cloud instances. Because all your virtual instance data is stored in persistent disks, it is crucial to understand how you can protect your data and make the most of features such as persistent disk encryption with Cloud Key Management Service (KMS).
This blog post describes the steps involved in this important security feature, which can be used in any deployment of NetApp Cloud Volumes ONTAP® for Google Cloud.
Encryption on Google Cloud Compute Engine
If you have been using Google Cloud for a while, you might have noticed some footnotes in the Cloud Console telling you that your data is encrypted. Contrary to other cloud providers, Google defaults to server-side encryption (SSE) using Google-managed encryption keys and does not allow you to disable it. You can, however, use Cloud KMS if you want more encryption capabilities or control over how your data is encrypted.
Cloud KMS supports different types of encryption keys:
- Generated key. You create and manage the key in Cloud KMS.
- Imported key. You create the key outside Google Cloud, and you manage it in Cloud KMS.
- Externally managed key. You create and manage the key outside Google Cloud by using your own hardware security module.
There are some significant differences between these options. It’s important to understand the drawbacks of each option so that you can choose the approach that works best for you.
Steps to Create and Encrypt a Google Cloud Persistent Disk Using Cloud KMS
Let’s take a look at how to encrypt your persistent disks by using Cloud KMS on Google Cloud.
1. In Google Cloud, navigate to the Security section on the left panel and find the Cryptographic Keys option.2. If it is the first time you’re visiting this section, the service is not immediately available. You must click Enable to use the Cloud KMS API.
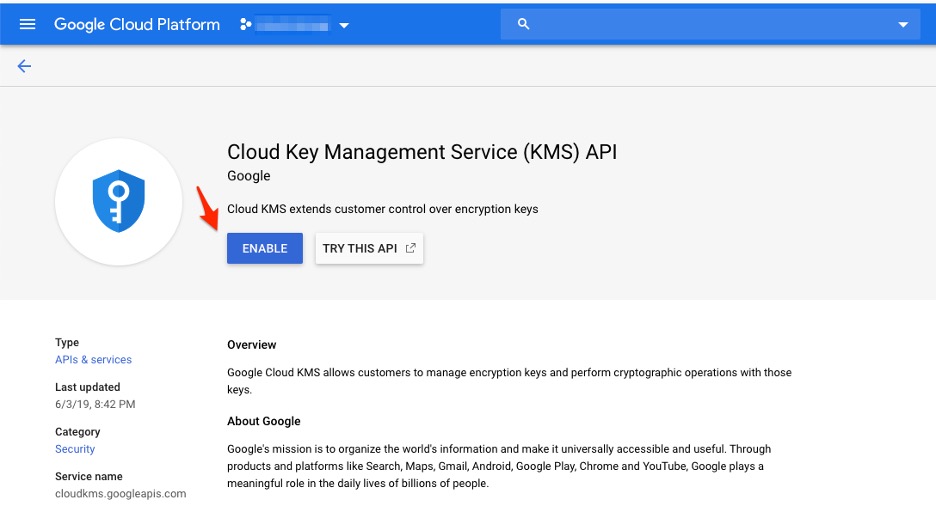
Cloud KMS API enablement.
3. Before you can manage any encryption keys, you must create a key ring. A key ring is a resource that contains at least one encryption key and helps you keep your keys organized.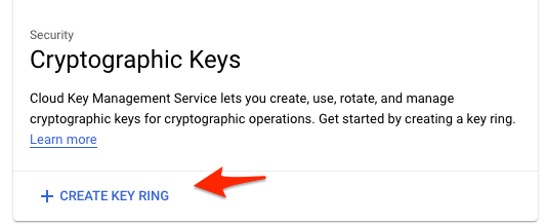
Cloud KMS Key Ring panel
4. A key ring requires a name and location. You can set the location as either global or associated with a particular region. If all the encryption keys in the key ring will be used to encrypt and decrypt resources in a given region, select that region as the key ring location.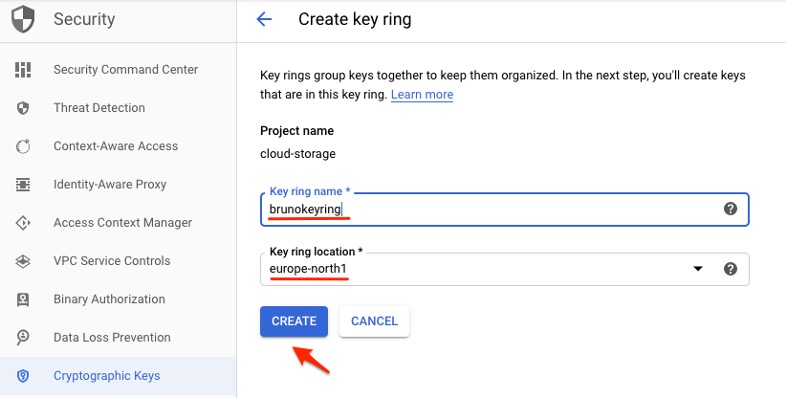
Key ring creation process
5. Now you can start to create keys or import keys into this key ring. Click Create Key.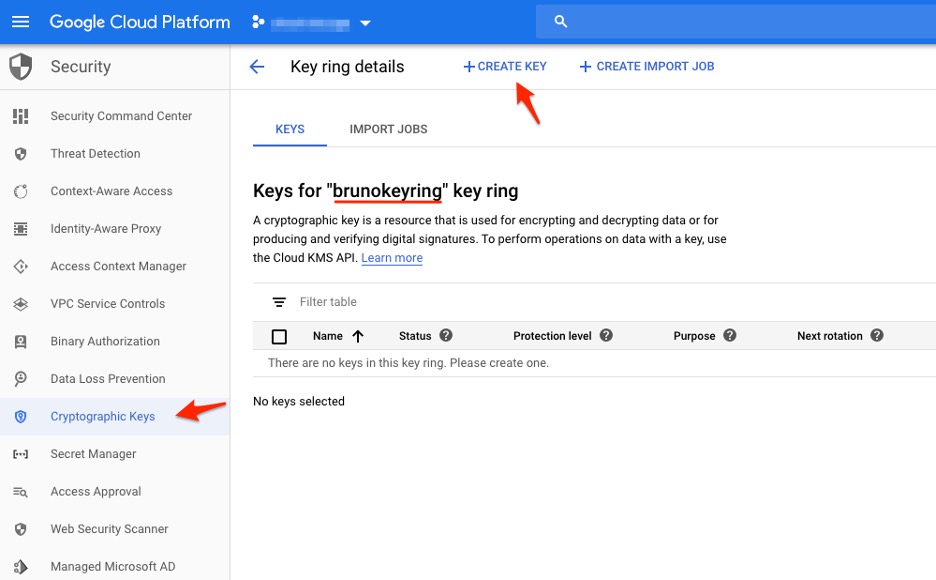
Key ring contents
6. Cloud KMS currently supports many types of keys. In this example, you can choose Generated Key, which is the standard type in Cloud KMS and the easiest to create and manage.7. Give the key a name. If you want, tweak the advanced options such as the protection level (software or hardware security module), purpose (symmetric or asymmetric), and key rotation parameters.
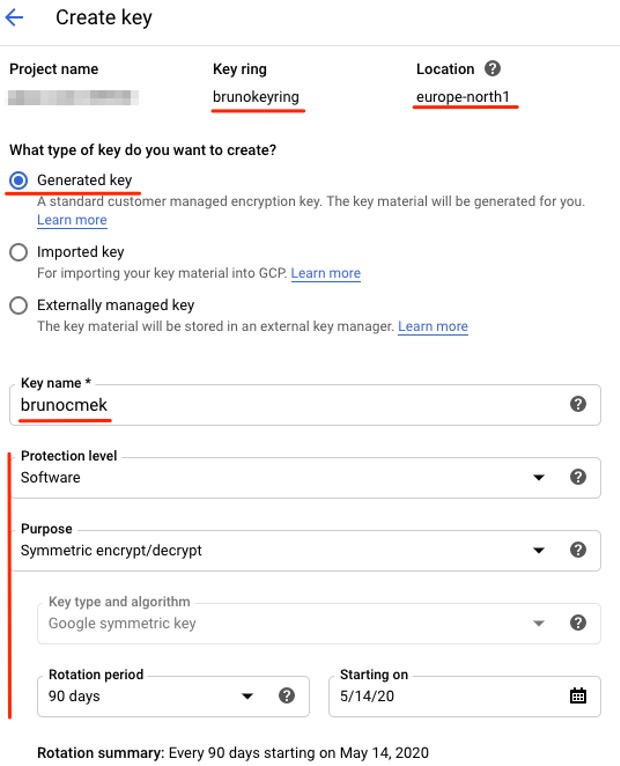
Key creation process
8. The key you just generated is now listed in the key ring. The key ring also indicates the key’s protection level and the date of the next automatic rotation.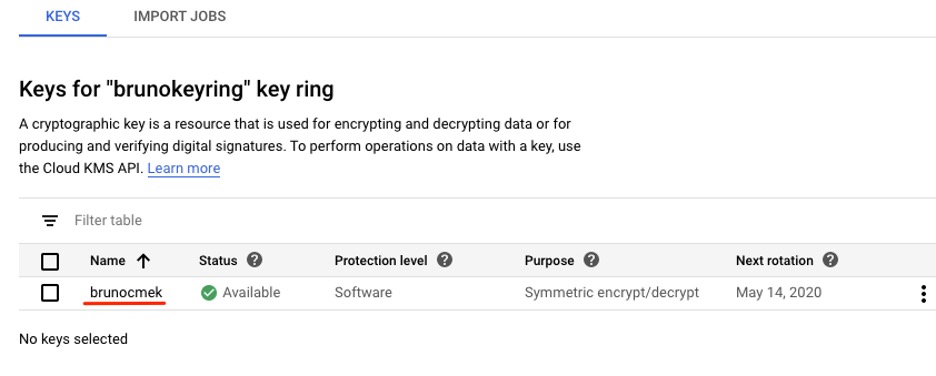
Keys available inside key ring
Using the Encryption Key with Google Cloud Compute Engine
To use your key, start by creating a Google Cloud instance. (An intuitive process, described in this blog post.) The encryption key will be used to encrypt the persistent disk of the instance.
By default, all persistent disks are encrypted by Google Cloud itself. However, if you want to encrypt them using keys that you create and manage (that is, using Cloud KMS), the instance creation process needs a small change.
1. In the instance creation panel, look for the Disks tab under the options listed as Management, Security, Disks, Networking, Sole tenancy.2. The Google-Managed Key option is enabled by default. Change this setting by selecting Customer-Managed Key, which will put Cloud KMS into use. From the drop-down menu, select the key you recently created.
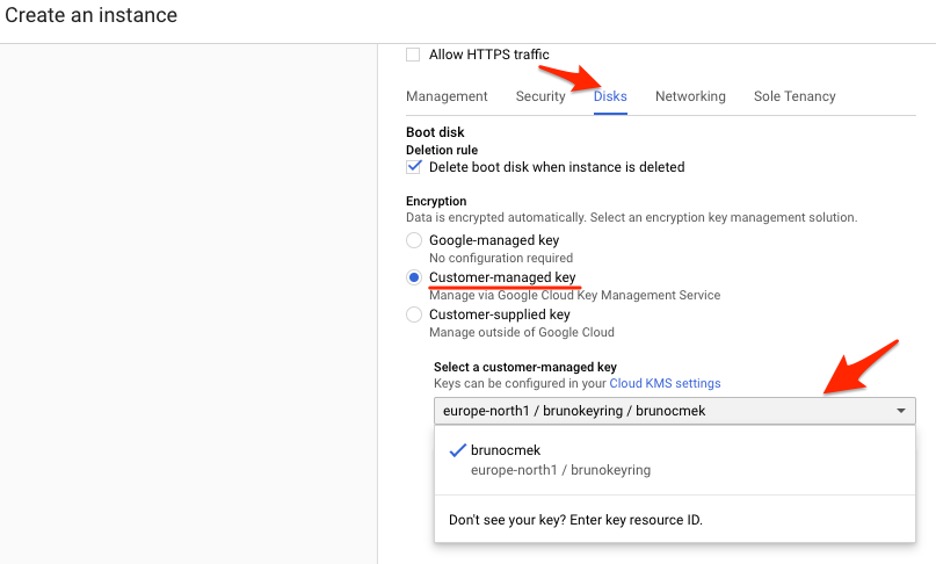
Instance creation with KMS encrypted persistent disk.
3. After you select a key, you are asked to enable permission to use Cloud KMS with Google Cloud Compute Engine. Click Grant.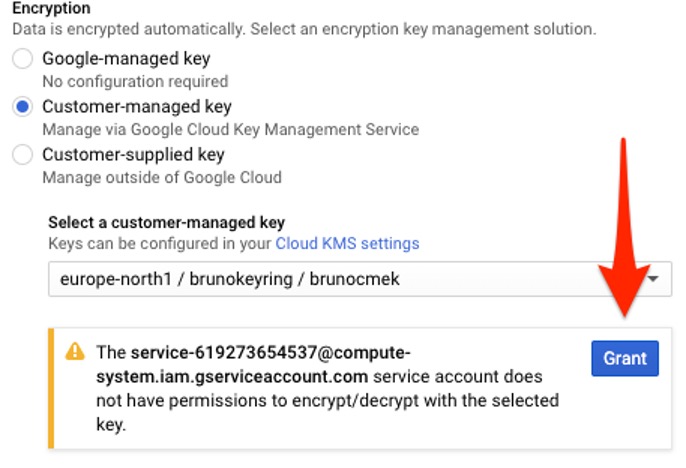
Granting KMS permissions to Compute Engine.
4. After you click Create and initiate the instance deployment, you are redirected to the VM Instances panel, where your instance soon appears.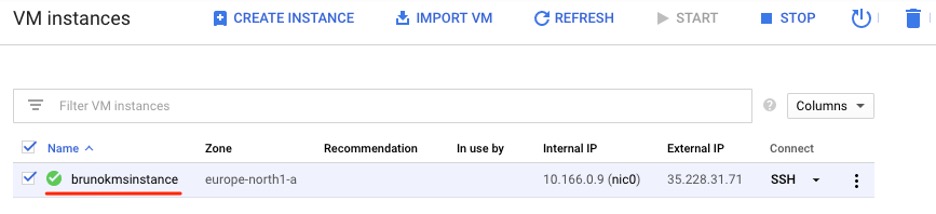
VM instance list
5. Navigate to Disks in the left panel and find the persistent disk that is connected to the Google Cloud instance. The disk details should indicate that it was encrypted using your customer-managed key.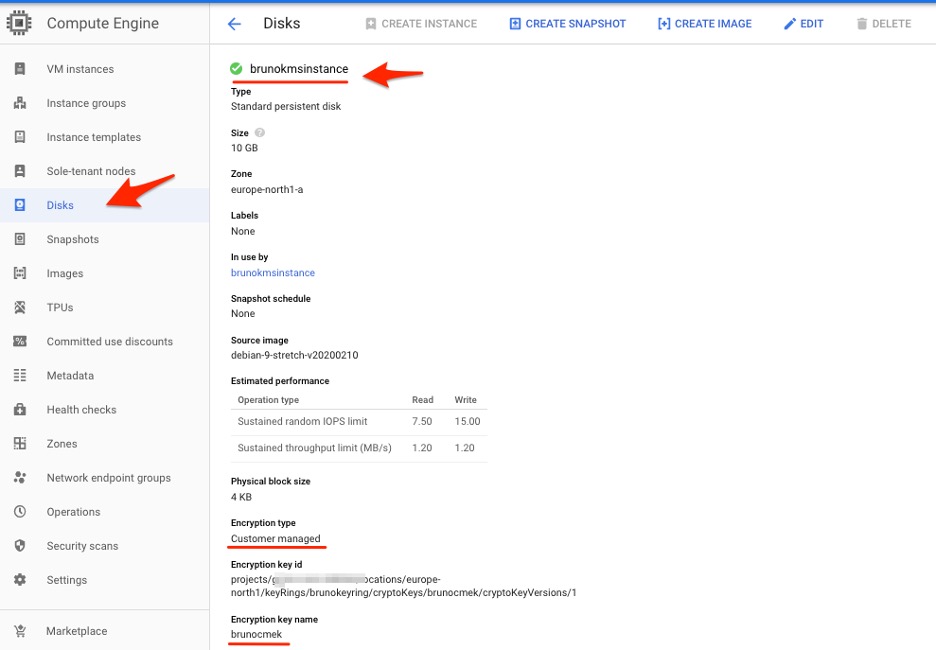
Persistent Disk details
Changing the Encryption of Existing Persistent Disks
After your Cloud KMS–encrypted Google Cloud instance is running, you might need to change its encryption keys, or even remove them completely. However, after exploring the Cloud Console, you will soon realize that by design it is not possible to simply change the disk encryption. You can, however, work around this situation.
Although the disk encryption can’t change, you can still create a virtual image from that persistent disk with automatic encryption. From the newly created virtual image, you can launch a new Google Cloud instance and select the encryption keys and method you want to use.
Conclusion
The baseline security configuration offered in Google Cloud is good in that your data is protected by default: Google-managed keys are there, and they can’t be turned off. However, you can take this encryption further by using Google Cloud KMS. Cloud KMS enables features such as managing your own encryption key, stronger encryption options, controlled rotation, and revocation mechanisms. These features are welcome, especially in the enterprise world, where compliance and security controls are often more strict.
It is fairly simple to start using Cloud KMS with Google Cloud Compute Engine. You can use the same encryption keys with other Google Cloud services, giving you a lot of control and security over your data. By understanding Cloud KMS and the pros and cons of each configuration option, you’ll be able to ensure your production data is secure. It’s a crucial capability for anyone using Cloud Volumes ONTAP on Google Cloud.
Try Cloud Volumes ONTAP for Google Cloud free for 30 days.

