More about NetApp Ransomware Protection
- What Should Your Data-Centric Ransomware Protection Include?
- Anti-Ransomware: Why Backup and Perimeter Protection Aren’t Enough
- The Zero Trust Model: What It Is and How It Affects Data Management
- Ransomware Protection Services and Solutions: A Market Overview
- IT & Ransomware: IT’s Role at the Forefront of Ransomware Protection
- Ransomware Detection: Techniques and Best Practices
- Data Security Capabilities Every IT Leader Needs To Know
- Ransomware Protection: Detection, Recovery, and Prevention
- Organization Security: Who’s Responsible for Keeping IT Safe?
- Ransomware Types: 5 Common Types of Ransomware Attack Top Security Tips for IT Teams
- Cyberstorage: Data-Oriented Security Designed for Ransomware Protection
- NetApp Ransomware Protection: A Complete Set of Data-Focused Protective Capabilities
- Ransomware Prevention and Remediation with Cloud Volumes ONTAP
Subscribe to our blog
Thanks for subscribing to the blog.
June 21, 2022
Topics: Data ProtectionAdvanced7 minute readRansomware ProtectionSecurity
As one of the biggest threats that an enterprise can face, there are a lot of different approaches to protect against and respond to ransomware attacks. But which is the right ransomware protection approach for you?
In this blog we review the different approaches that are being taken by ransomware protection services and solutions and delve into the promising new approach to fighting ransomware: cyberstorage.
Read on as we cover:
- Ransomware on the Rise
- The Ransomware Protection Software Market
- Users: Security Teams Versus IT Teams
- Coverage: Single-Purpose Tool Versus Comprehensive Ransomware Protection Solution
- A New Ransomware Protection Option: Cyberstorage
- NetApp Ransomware Protection Service: Your Cyberstorage Solution
- Take the Next Step in Ransomware Protection
Ransomware on the Rise
In case there was any need to restate the point, ransomware remains one of the most serious cyber threats that enterprises face today. And it’s getting worse—ransomware is measurably on the rise. The numbers are compelling:
- In 2021 ransomware played a role in 10% of data breaches, which is a 2X increase year-over-year (Verizon 2021 Data Breach Investigations Report)
- A little over one-third (37%) of companies worldwide were subject to some form of ransomware exploit (IDC 2021 Ransomware Study)
- In the US alone there were 2,084 ransomware attacks registered from January through July 2021—a 62% increase over the same period in the previous year (FBI Internet Crime Complaint Center)
The market has responded with a wide range of ransomware protection services, which we’ll take a look at below.
The Ransomware Protection Software Market
As shown in Figure 1, the ransomware attack protection market can be classified according to two characteristics:
- Users: Which target users they approach: security teams versus I&O teams
- Coverage: How comprehensive the product is. Is it a tool focused on a single capability or a complete solution
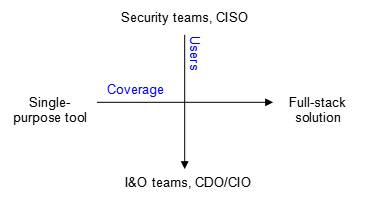
Figure 1: The Ransomware Protection Software Market, by users and coverage
Users: Security Teams Versus IT Teams
The majority of companies offering ransomware protection target the security teams and the CISO with cybersecurity solutions. These companies are essentially perimeter security vendors that initially provided corporate network firewalls. However, with the emergence of the public cloud and cloud-native technologies, these companies have evolved to protect “modern” perimeters, such as network micro-segments, end points, and cloud-native workloads including containers, microservices, and serverless functions.
These vendors offer security teams comprehensive XDR (extended detection and response) solutions that can identify even the most sophisticated threats, track them across complex environments, accelerate time-to-response and time-to-remediation, and support cybersecurity forensics. But XDR solutions are focused on protecting the network’s perimeter. In most cases, once that perimeter is breached, the attacker has access to the data, which is the prime target of any ransomware attack.
If the target is data, it’s the data owner’s responsibility to protect it.
For that reason there are numerous data-centric ransomware solutions offered for the I&O (infrastructure and operations) team and the CDO/CIO. These solutions offer protection against ransomware through backup and disaster recovery capabilities that quickly restore business continuity, data privacy and data loss prevention guardrails that enhance the organization’s security posture, and centralized data storage management across complex hybrid infrastructures.
But here again, there are challenges. Although backup is a good last line of defense,, to gain high data security posture a ransomware protection plan must go beyond backup. Ransomware protection tools must also be able to prepare for attacks, identify them as they take place, and have a way to stop them.
Coverage: Single-Purpose Tool Versus Comprehensive Ransomware Protection Solution
Of the companies that pitch their cybersecurity ransomware protection services and solutions to security teams, some offer a single-purpose tool, such as a web application firewall or a penetration testing tool. Others offer an integrated suite of tools that, together, deliver a more end-to-end cybersecurity solution, including ransomware protection.
The data protection companies that offer anti-ransomware capabilities to I&O teams can be categorized into three segments as far as coverage is concerned:
- Backup and restore specialists: Backup and restore are important elements of any anti-ransomware program, ensuring that blocked or frozen data can be recovered quickly, with minimal data loss.
However, they should really be the last line of defense. The goal should be to thwart ransomware access to data assets long before data is actually taken hostage. Backup solutions on their own do not provide sufficient layers of anti-ransomware defense for the organization’s data.
- Data management solutions that evolved from backup: Companies that offer a wide range of data protection capabilities—from automated discovery and classification to backup and restore—can deliver effective anti-ransomware coverage.
However, most of these companies started in the backup domain and that remains their real strength. These solutions have added important capabilities in order to provide broader coverage, but they still do not add up to a full-stack anti-ransomware solution, and are missing capabilities such as UBA (user behavior analytics), sensitive data discovery, permission analysis, and other data governance capabilities.
- Data mapping and classification specialists: Having full visibility into data assets across complex hybrid infrastructures is key to fighting ransomware. It’s also important to categorize data based on risk profile. Tools that let you map and classify your data help you stay aware of your data can help you understand which data needs protection, differentiating between high-risk/low-risk hot/cold data.
But automated data discovery and categorization on their own do not provide complete anti-ransomware coverage. They have zero capabilities related to backup and data resilience, and certainly no capabilities to create snapshots or immutable copies of the data.
- Cyberstorage solutions: Cyberstorage is an evolving concept of full and integrated sets of capabilities to prepare, identify, protect, and recover data assets.
These solutions are able to let IT teams manage the data security posture of the entire company from a single pane of glass.They are focused on data protection capabilities and are aimed at offering I&O teams a complete set of tools to protect against ransomware.
A New Ransomware Protection Option: Cyberstorage
Cyberstorage is a new approach to security, giving I&O teams the ability to integrate their storage and security capabilities to define a better defensive posture against ransomware and other major cyber threats.
Since those threats are diverse, cyberstorage capabilities are wide-ranging, incorporating everything from vulnerability scanning, permission controls, automatic monitoring for suspicious activities, to traditional remediation features like backups and failover processes.
What I&O teams get is a centralized platform to carry out all of the protection activities in the data estate. This translates to more control, more visibility, fewer points of failure, and less overhead.
Cyberstorage solutions have built-in and proactive capabilities for identifying, blocking, responding to, and recovering from ransomware attacks.
In short, cyberstorage solutions enhance a storage system’s existing data protection activities, allowing I&O and storage teams to contribute an additional and significant layer of cyber resilience.
Cyberstorage positions the IT team as an essential player in ransomware protection at a time when changing work patterns have made systems more vulnerable than ever to ransomware and other cyber exploits.
Cyberstorage solutions allow IT to reduce the risks of ransomware attacks and restore data quickly when attacks occur. Any effort by IT to reduce the threat of data corruption improves the organization’s overall posture.
NetApp Ransomware Protection: Your Cyberstorage Solution
As a global leader in the data management domain, NetApp is well positioned to offer I&O and storage teams a full-featured cyberstorage solution for next-generation ransomware protection services.
NetApp Ransomware Protection offers full cyberstorage capabilities for users both on-prem and in the cloud to both defend against and prevent ransomware attacks:
Netapp Ransomware Protection is a comprehensive set of data-centric capabilities, allowing to protect your data estate with a zero-trust approach from the inside out. It enables you to map and classify your data, detect abnormal user activity, manage access, and avoid costly downtime with rapid backup and restore. IT teams can use these advanced defense mechanisms to strengthen cyber resiliency and make sure the most critical data stays protected.
Take the Next Step in Ransomware Protection
NetApp’s data-centric ransomware protection solution takes a zero-trust approach to manage and monitor storage infrastructure at scale, ensuring that best practices are in place to block ransomware attacks. But if data is breached, NetApp makes sure that recovery is quick and comprehensive.
Learn more about NetApp Ransomware Protection here.

